Technological developments usher in a new era of innovative security measures that transform business operations. However, as technology and data security measures advance, so do cyber threats.
With digital hacking methods becoming increasingly sophisticated, cybercrime incidents are also rising. Recent statistics show that 60% of cyber attacks happen via mobile phones, deviating from the typical computer and laptop modus operandi.
Fortunately, security options such as SMS 2FA or text message authentication allow your business to add another layer of safety for your clients. Read below to learn what SMS 2FA is and how it can enhance data security measures.
What is SMS 2FA?
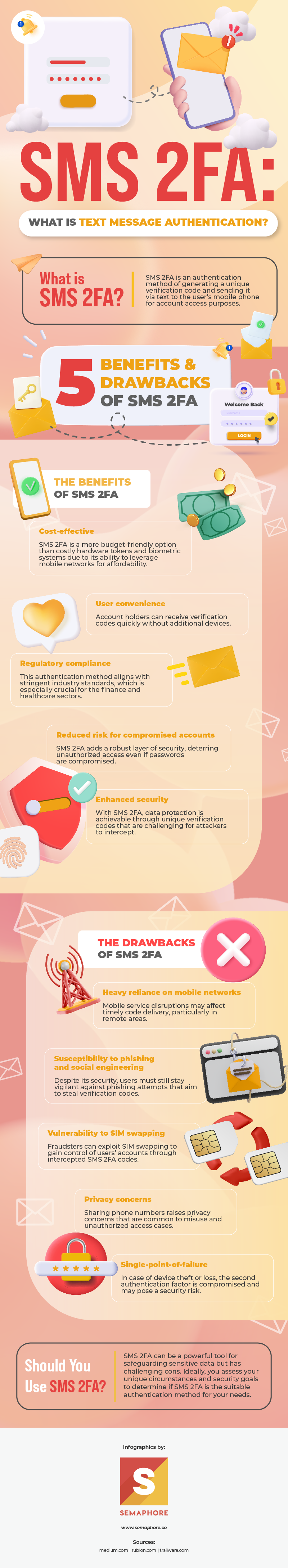
SMS 2FA, or short message service two-factor authentication, is a cybersecurity mechanism that generates a one-time code to verify a user’s identity during login or sensitive transactions.
In a world where cyber threats are ever-present, incorporating this authentication measure is an excellent tool to safeguard your users’ data online.
To understand SMS 2FA further, you must know how it works.
How SMS 2FA Works
This authentication method implements an extra layer of security to beef up the traditional username and password login process. Here’s a step-by-step process of how it works.
- The SMS 2FA method begins upon entering a username and password during login in an online platform.
- After this initial step, the server will generate a unique one-time verification code (OTP).
- The code goes directly to the user’s mobile phone as a text message.
- Next, the message will instruct the recipient to enter the code into the login page for identity confirmation.
- If the code matches the one generated on the server, the person requesting account access will receive the authorization. Otherwise, the system will deny the request.
Two-Factor Authentication vs. Two-Step Authentication
People often use the terms two-factor authentication and two-step authentication interchangeably. However, there are subtle differences that you must know to help you choose the suitable method for your authentication needs.
Firstly, a 2FA method requires two authentication factors to access an account. For SMS 2FA, the elements are typically information known only to users⎯such as the password⎯and “something they have,” like the mobile phone containing the verification code.
Conversely, the two-step authentication method can involve two factors of the same type. For instance, entering a password will prompt an email with a verification link sent to the user’s inbox.
While it adds an extra step for security since only the user knows these details, it may not incorporate the something-you-have aspect of a 2FA.
Additionally, knowing a user’s password is insufficient in the SMS 2FA method. Anyone attempting to access the user’s account will still need access to the mobile phone with the unique code.
The technique adds a safeguard powerful enough to deter unauthorized access, making it a valuable tool for protecting sensitive business data.
5 Benefits and Drawbacks of SMS 2FA
An SMS 2FA is a versatile cybersecurity tool. It offers several advantages to users, but it’s not without its drawbacks. You must be aware of its limitations and take steps to mitigate potential risks so your business can fully reap the benefits of this authentication method.
The Benefits of SMS 2FA
1. Cost-effective
Often, hardware tokens and biometric systems can be expensive to implement. Luckily, SMS 2FA is remarkably more cost-effective than other authentication methods.
It utilizes the infrastructure of mobile networks and the commonality of mobile phones, making it an affordable choice for your business.
2. User convenience
For most people, having a mobile phone is necessary. So, there’s typically no need for additional hardware or complex setups. You can send verification codes directly to your customers’ mobile devices, simplifying the authentication process.
3. Regulatory compliance
Many industries have stringent security standards, especially in the finance and healthcare sectors, which deal with vast amounts of sensitive data. Fortunately, SMS 2FA allows you to meet these requirements sufficiently.
Its robust authentication mechanism aligns with many regulatory guidelines to ensure your organization stays on the right side of the law.
4. Reduced risk for compromised accounts
By introducing a second authentication process, this verification method can significantly reduce the risk of unauthorized access to users’ accounts.
Even if malicious actors somehow obtain account passwords, they’ll still need access to the mobile phone for the code that will complete the login process. This extra layer of security can effectively prevent breaches.
5. Enhanced security
SMS 2FA bolsters data security. It’s a simple yet effective way to protect sensitive information. The uniqueness of the verification codes and their limited validity window make it challenging for attackers to predict or intercept them.
The Drawbacks of SMS 2FA
1. Heavy reliance on mobile networks
While SMS 2FA is accessible for most users, disruptions in mobile services or poor network coverage can hinder the timely delivery of verification codes. As such, those in remote areas or regions with less reliable networks may face challenges with this method.
2. Susceptibility to phishing and social engineering
Incidents of scam calls like voice phishing are common nowadays. These scams remain a significant threat, even with SMS 2FA in place. Cybercriminals can still trick users into revealing their verification codes by impersonating your organization.
3. Vulnerability to SIM swapping
In a SIM swapping attack, fraudsters trick mobile carriers into transferring a user’s phone number to a new SIM card under their control. In effect, they can receive SMS 2FA codes and access the owner’s account.
4. Privacy concerns
Often, the process for SMS 2FA involves sharing a phone number. However, some users may have privacy concerns, especially with many businesses misusing phone numbers or others gaining unauthorized access to this information.
5. Single-point-of-failure
The SMS 2FA method is not immune to single-point-of-failure risks. Say a user’s mobile phone gets stolen or lost. The second authentication factor is compromised since other unauthorized users can access the verification codes.
Should You Use SMS 2FA?
Undoubtedly, SMS 2FA can be a powerful tool that keeps users’ data safe from the ever-growing cases of data breaches.
It’s a cost-effective and user-friendly solution that can enhance the security of user accounts and business processes. For many, it provides an accessible and effective way to bolster security.
However, its reliance on mobile networks and susceptibility to phishing attacks, SIM swapping, and data privacy concerns can impede the SMS 2FA’s effectiveness.
As such, you must take the proper measures to address these issues. If you belong to organizations in high-security environments, you may opt for more advanced authentication methods.
Whether to use SMS 2FA depends on assessing your unique circumstances and choosing the best solution for your security goals.
Safeguarding Your Business’s Data
SMS 2FA is a valuable tool in today’s ever-evolving cybersecurity landscape and offers benefits that can prevent cyber threats from hampering your operations. However, it doesn’t come without drawbacks.
So, assess your needs first before implementing this method.
Remember, informed choices today can secure your digital world tomorrow. Partnering with a data-driven SMS marketing solutions firm like Semaphore can help your business safeguard customer data.
Make the most of your SMS campaigns with Semaphore. Contact us today to know more.
